Each venture has its points. Points are issues that come up in the course of the execution of the venture. Plan as totally as you want, you’re nonetheless going to face issues, even in the event you use venture planning software program. Issues throughout a venture are a given, and fixing them in actual time whereas sustaining venture progress is an actual problem.
Dangers are a bit completely different than points; dangers are points that haven’t occurred but. By figuring out what dangers are possible, you possibly can put together for them and have a response in place if and once they present up in your venture.
However as soon as the plan is in place, and also you’ve detailed all of the dangers more likely to happen over the life cycle of the venture, the following step is having a system in place to watch and monitor the dangers which may occur, and the problems that do. That’s referred to as threat or difficulty administration. However you possibly can take that administration even additional by utilizing what’s referred to as a RAID log.


Get your free
RAID Log Template
Use this free RAID Log Template for Excel to handle your initiatives higher.
What Is a RAID Log?
RAID is an acronym that stands for Dangers, Actions, Points and Choices.
- Dangers are the potential issues lurking in your venture. Dangers are usually regarded as hurting the venture, however there are additionally optimistic dangers.
- Actions are what you should do all through the venture.
- Points are when one thing goes mistaken within the venture. If a problem isn’t managed and resolved it could derail the venture or trigger the venture to fail.
- Choices are the way you determined to behave within the venture.
A RAID log, subsequently, is a venture administration software that tracks dangers, actions, points and selections. It’s a easy approach to arrange this data and turns out to be useful throughout conferences and venture audits.
Utilizing a RAID log is an effective begin, however venture administration software program is extra thorough. ProjectManager is award-winning venture administration software program that has threat administration options that aid you determine, monitor and mitigate threat, points and modifications in your venture. Create dangers or points as you’d a activity. You possibly can add tags to make it simpler to search out by filtering after which view the danger throughout our Gantt chart, record, board and calendar views. Generate experiences to trace your progress and extra. Get began with ProjectManager immediately totally free.
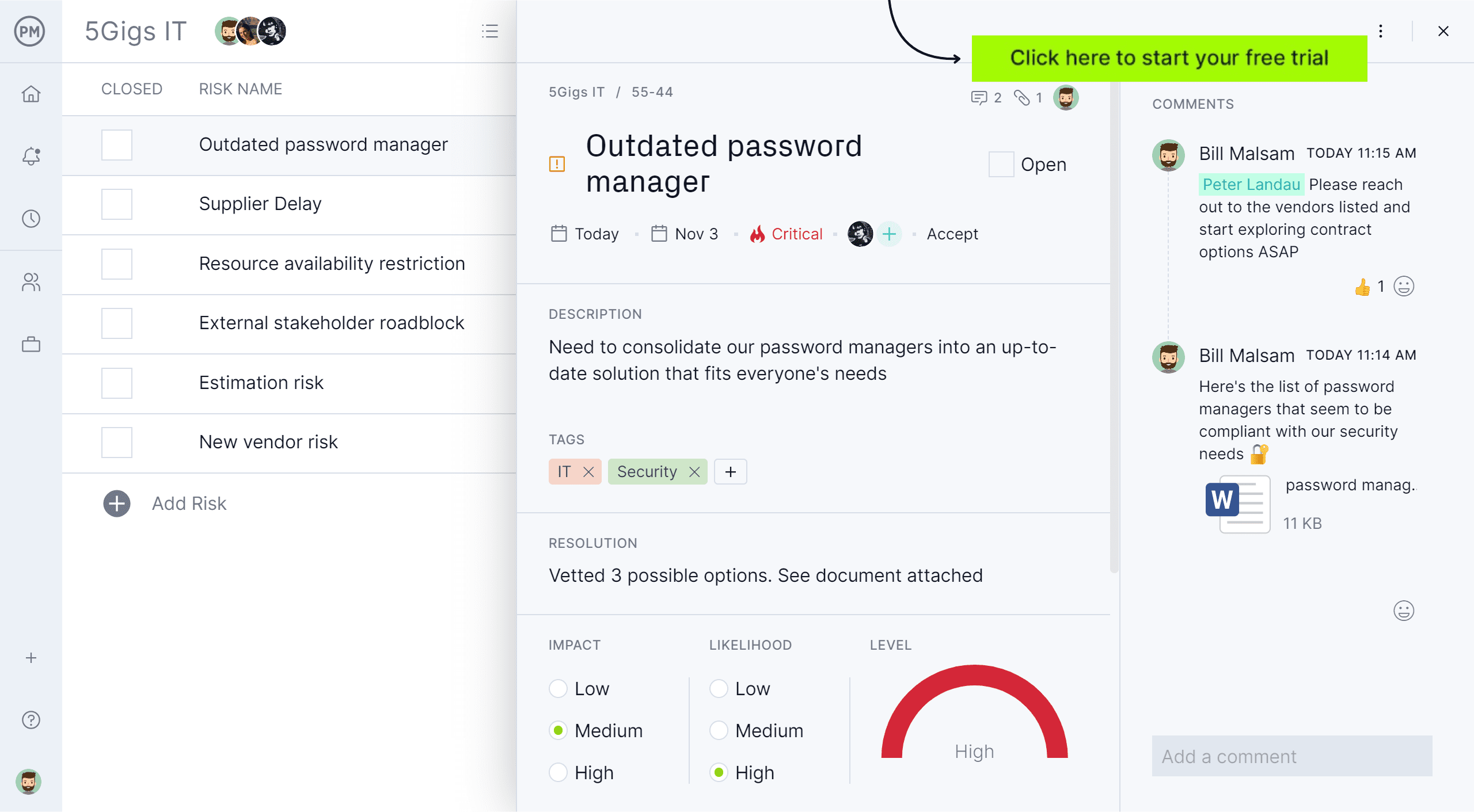

Learn how to Use a RAID Log
A RAID log is pretty easy to make use of. Begin by filling in data for the 4 subjects listed above: dangers, actions, points and selections.
Dangers
With dangers, you record people who suppose would possibly happen over the life cycle of the venture. For every of the dangers, you observe the chance of it really taking place. Then write what actions you intend to take if it does present up and the way these actions will resolve it.
Every venture threat ought to be given to an proprietor who’s answerable for catching the danger if it turns into a problem, and for implementing the plan to resolve it. You may as well arrange overview dates to watch the progress of that repair or simply examine in often to see if the danger has elevated or decreased in its chance.
Actions
For the actions part, there wants an proprietor, too. The proprietor can be assigned to each motion merchandise that you just listed that must be accomplished. Having an proprietor makes positive that the motion is managed and won’t fall via the cracks of a busy venture.
The actions, no matter they’re, have to be charted. That’s famous on the date they’re accomplished. Throughout venture conferences, consult with this record and examine off these actions which have been accomplished to ensure there’s been follow-through.
Points
Points come up in a venture, and each must be recognized right here. Notice what the plan is for coping with the difficulty, who’s going to guide that difficulty administration initiative, what the schedule for overview can be and the way it is going to be marked accomplished when resolved.
Choices
As for selections, once more that is merely an inventory of choices that have to be made all through the venture. Think about it a approach to acquire the thought technique of the venture, a report of what selections had been made, who made them and why.
As you possibly can see, a RAID log is merely a way for maintaining all this data organized and simply managed in the course of the venture. It’s not arduous to be taught however it may be considerably of a hurdle to clear at first. However when you get used to maintaining a paper path of those 4 subjects, it’ll turn into second nature and show an asset.
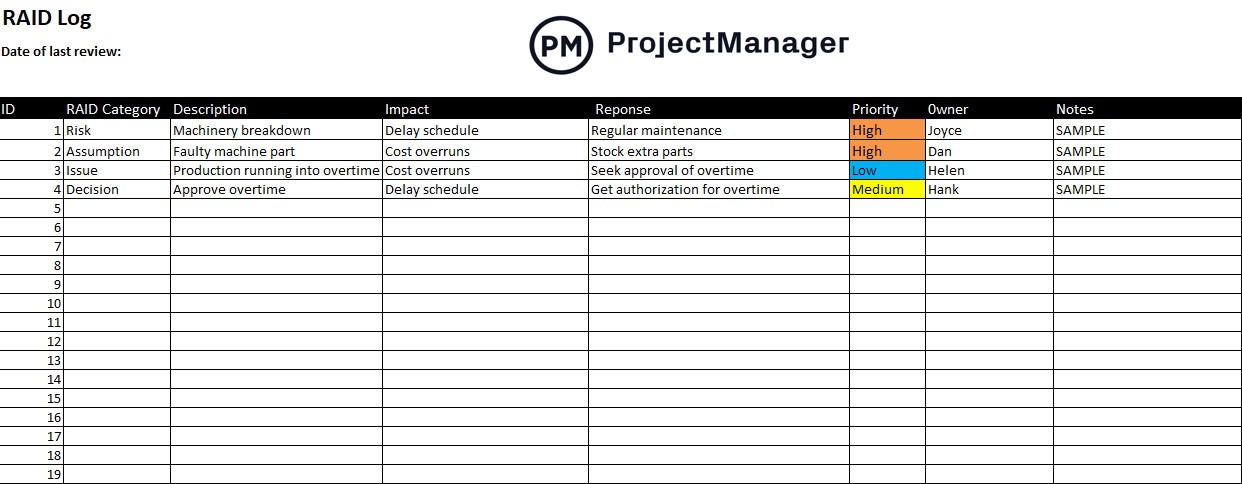
RAID Log Template
This RAID log template lets you record down your venture dangers, assumptions, points and selections. As well as, you possibly can describe their influence, response actions, precedence and who’s answerable for them.

Who Ought to Use a RAID Log?
Mission managers use a RAID log to assist oversee components that would influence a venture, comparable to threat, assumptions and dependencies. This enables them to raised distribute duties, justify their selections and consider the success of their efforts.
Enterprise analysts use a RAID log to grasp enterprise necessities, assess dangers and determine points and dependencies. A threat supervisor will use the RAID log to assist determine, assess and prioritize dangers, which helps to develop higher methods to mitigate these dangers.
Crew leaders and supervisors can hold monitor of their staff’s duties, determine potential points and be certain that initiatives are shifting ahead as deliberate. A RAID log helps leaders arrange data to share with their staff so everybody understands the venture’s objectives and methods. That is additionally true for purposeful division managers in any firm in addition to operations managers and even executives.
When to Make a RAID Log in Mission Administration
A RAID log is used when managing advanced initiatives with a number of variables that would influence the venture’s success. They’re additionally helpful for organizing agile initiatives, particularly when documenting motion objects and when there are bigger venture groups.
Throughout periodic evaluations, a RAID log is used to evaluate the standing of every issue and have interaction stakeholders within the overview course of. The RAID log is extra complete than a threat register as a result of it consists of assumptions or actions, a problem log and dependencies or selections along with documenting dangers. They will get sophisticated, which results in data overload.
RAID Log Instance
To raised illuminate the RAID log and the way it’s used, let’s think about a real-life building venture instance. Acme Building is constructing a manufacturing facility, however after negotiating with distributors they count on a possible value enhance for lumber, which can threaten their price range and revenue margin. There is also a scarcity, which can result in delays and different dangers related to venture supplies. There are different potential dangers comparable to adversarial climate circumstances, equipment breakdown, labor shortages and subcontractor default.
Utilizing a threat matrix, they instance the potential influence on the venture and with that information create a threat mitigation technique, which is to hunt out a number of distributors to assist Acme negotiate a extra aggressive value for the lumber, discover new provides and so forth.
This threat administration plan is made out so Acme has connections with these secondary distributors in case there’s a value hike. As they plan, a call matrix helps them choose one of the best plan of action. With that information, they develop an motion plan and all through the venture replace the RAID log to make sure they’re prepared if the value spikes or supplies are sparse. Right here’s what this RAID log instance takes care of a few of these dangers have turn into points.
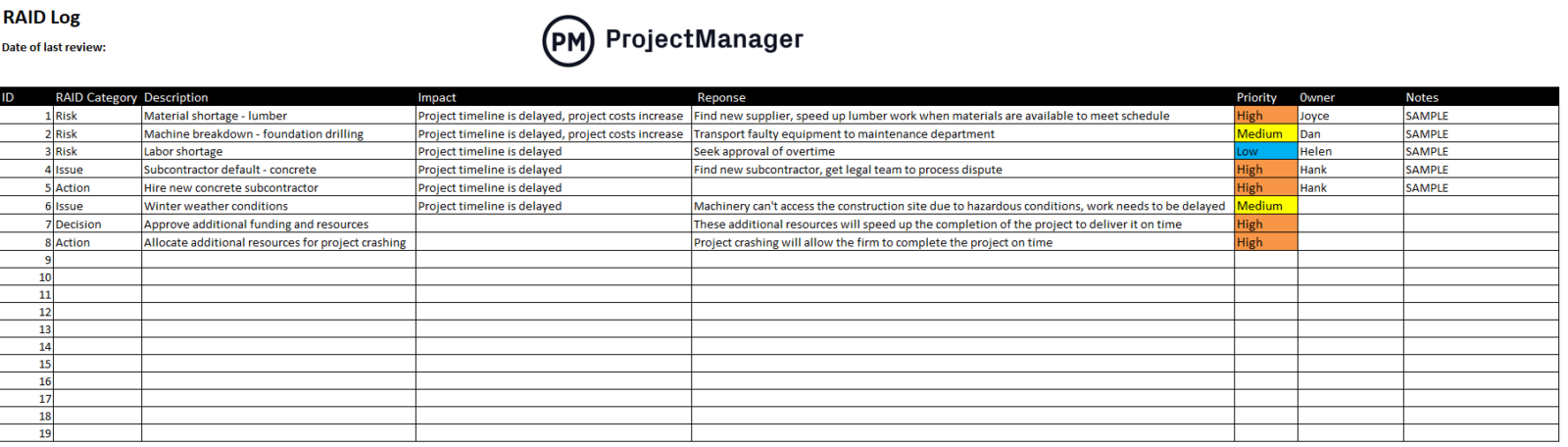

As might be seen within the RAID log above, the potential dangers that had been recognized earlier than the venture execution section began grew to become points that delayed the venture schedule. Due to this fact, the development venture administration staff determined to allocate further assets to hurry up the execution of the venture in order that it may be delivered on time.
Learn how to Make a RAID Log Step-by-Step
Right here’s a extra detailed description of every step within the course of of creating and updating a RAID log all through a venture.
1. Establish Dangers By Making a Danger Breakdown Construction (RBS)
A threat breakdown construction is a chart that helps venture managers determine and arrange dangers in a venture. It lists dangers so as of chance and serenity and teams them by sort. This helps to cowl all venture dangers.
2. Analyze Potential Dangers with a Danger Matrix
A threat matrix is a software that helps analyze potential dangers by assessing their chance and severity throughout venture planning. It begins by figuring out dangers, figuring out the chance of that threat occurring, assessing its influence, assigning a threat rating and mapping out and prioritizing dangers.
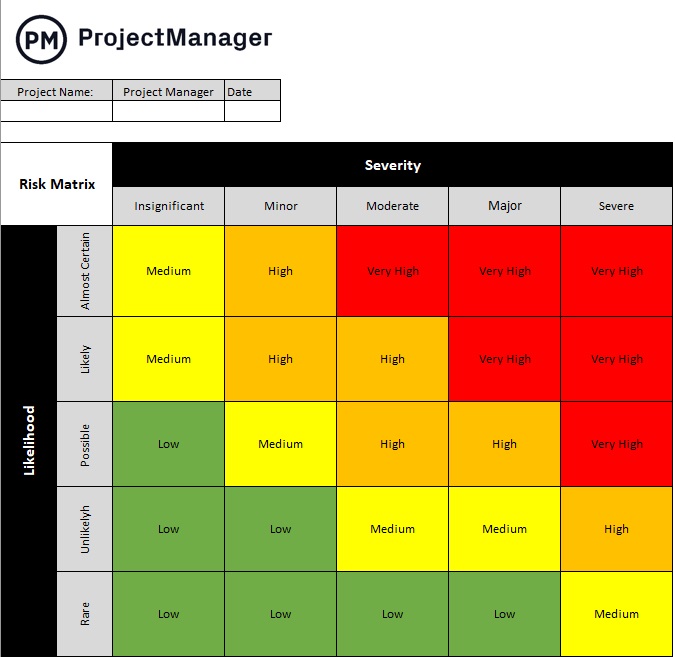

3. Plan Danger Mitigation Methods
As soon as dangers are recognized and the chance of their incidence and, in the event that they do, what influence they’ll have on the venture has been listed, it’s time to determine what to do if the danger turns into an precise difficulty. It is a threat mitigation plan and having one in place earlier than the danger happens helps groups reply rapidly and successfully.
4. Write a Danger Administration Plan
To mitigate the danger, a threat administration plan is required. This course of consists of figuring out the dangers, assessing them and methods to mitigate them. Assigning duties for duties to staff members who can be answerable for mitigating the difficulty. Then develop contingency plans simply in case. Be sure you talk the plan and prepare workers to reply successfully. And all the time be monitoring for brand new dangers.


5. Use a Choice Matrix to Select the Greatest Answer to Points as They Happen
A call matrix lists all of the choices and components that have to be thought-about when responding to a problem. These are scoured and weighted by the relative significance of the issue. Including these scores helps to offer an total rating for every possibility.
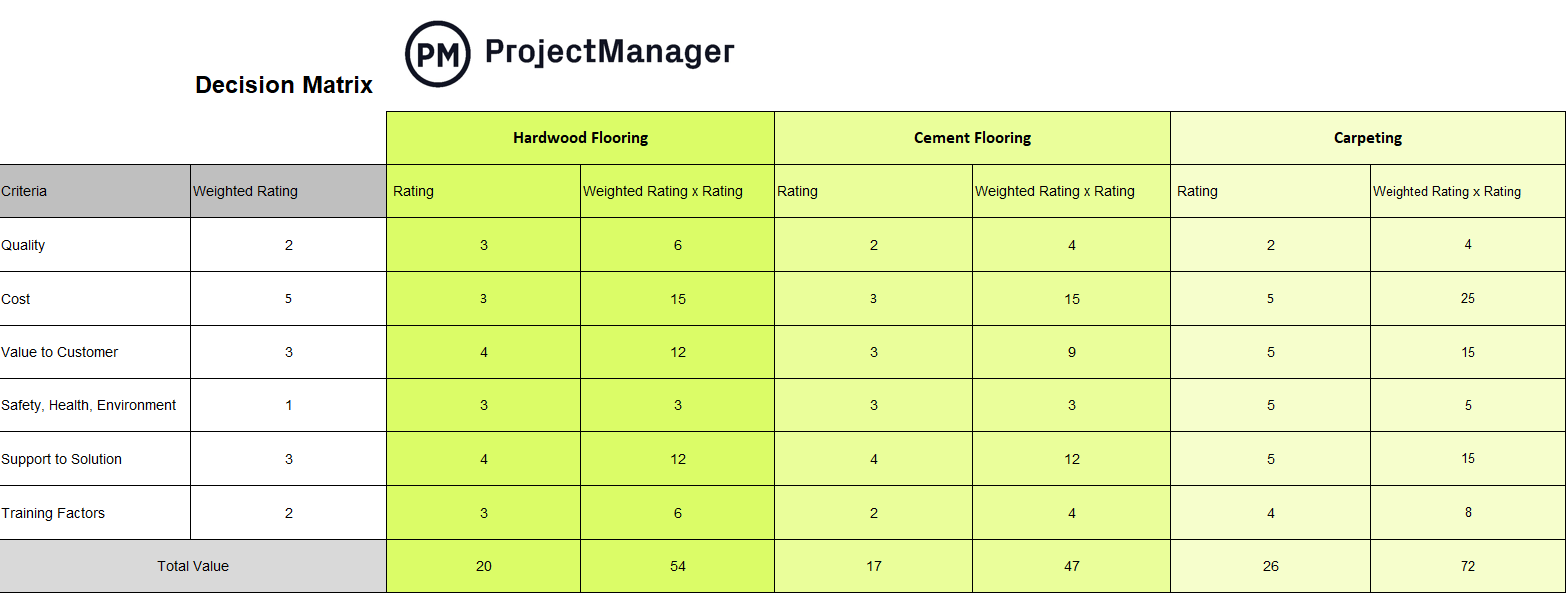

6. Make an Motion Plan for the Mitigation of Points
As soon as dangers have been recognized and a mitigation technique has been decided, an motion plan is created. It is a sequence of steps or duties that can be carried out by assigned staff members to mitigate the danger. Managers will monitor this to make sure that it’s being carried out accurately and promptly.

7. Replace and Monitor the RAID Log All through the Mission Life Cycle
A RAID log shouldn’t be accomplished as soon as however is a dwelling venture administration doc. It ought to be reviewed and up to date all through the life cycle of the venture. The extra present the info collected within the RAID log, the extra possible the venture will have the ability to deal with points as they come up.
Professionals and Cons of Utilizing a RAID Log
There’s by no means a magic bullet that may pierce all issues, and a RAID log isn’t any completely different. There are professionals and cons to utilizing this venture administration chart.
Professionals
The obvious profit is {that a} RAID log makes you suppose in an organized and strategic manner a few venture. It helps you acquire a mass of information that will be extremely unlikely to stay in a single’s head with out some methodology to gather them.
Think about the RAID log a shortcut, and any busy venture supervisor will admire that, as time is treasured when managing a venture. It’s additionally a shortcut for communications, as the data you collect shouldn’t be simply disseminated to those that have to realize it.
Piggybacking on that professional is the truth that a RAID log helps you preserve management over the venture. Most questions you would possibly get from a stakeholder are going to be answered within the RAID log, which implies much less working round attempting to determine issues out.
Mainly, you’re controlling the info of your venture so it’s simply accessible. There’s all the time loads of data spinning across the venture, so that is an asset. Plus, as dangers materialize and points come up, you could have a system to manage and monitor them, so that they don’t sideline the venture.
The RAID log is a template to seize these plans and, higher nonetheless, a ruler to measure how successfully they’re being carried out. With each threat having a venture member answerable for figuring out and resolving it, you’re going to, once more, have extra management over the venture and the method of threat administration.
With a RAID log, your decision-making is extra constant. A venture is made up of a swarm of planning selections, and that’s simply in at some point, so whereas there are minutes in conferences, the RAID log captures these selections which might be happening in a extra casual setting. Now you and your stakeholders have an in depth report of all the choices that happen over the life cycle of the venture, with reasoning as to why they had been made, when and due to what.
What assumptions had been made in the course of the venture? There are lots, however now you don’t should depend on somebody’s reminiscence to retrieve them. Whereas some may be unimportant, others should not, and it isn’t all the time clear on the time which is which.
Cons
Generally, on a bigger venture, the RAID log must be reviewed typically. The frequency of those evaluations could make it really feel as in the event you’re continually trying over the RAID log.
Due to this fact, it’s straightforward to get misplaced within the particulars. So, the easiest way to method a RAID log is by having a good suggestion of how deep into the woods you need to go together with every of those topics. Too far and also you’re going to lavatory down and miss the essential stuff. However in the event you’re too cursory in your method, then it defeats the aim of the RAID log and just about renders it ineffective.
What’s an excessive amount of data and what’s too little? That may typically be clearest in hindsight, although, and also you don’t have the posh of managing a venture backward. You possibly can prioritize the problems as excessive or low, which is one approach to decide how a lot knowledge can be required.
Additionally, you should method every part of your RAID log with a special mindset. Points are completely different than dangers, for instance. Perhaps you need to hold a sequence of RAID logs, one for every part, somewhat than combining the 4 classes into one log.
ProjectManager Helps Flip Cons into Professionals
A RAID log may very well be so simple as a spreadsheet. All you want is a spot to avoid wasting the collected knowledge. However that’s the minimal, and in case you have extra dynamic software program then you could have a extra dynamic RAID log. ProjectManager is cloud-based venture administration software program that delivers real-time knowledge that can assist you determine, monitor and mitigate dangers, points and modifications in actual time.
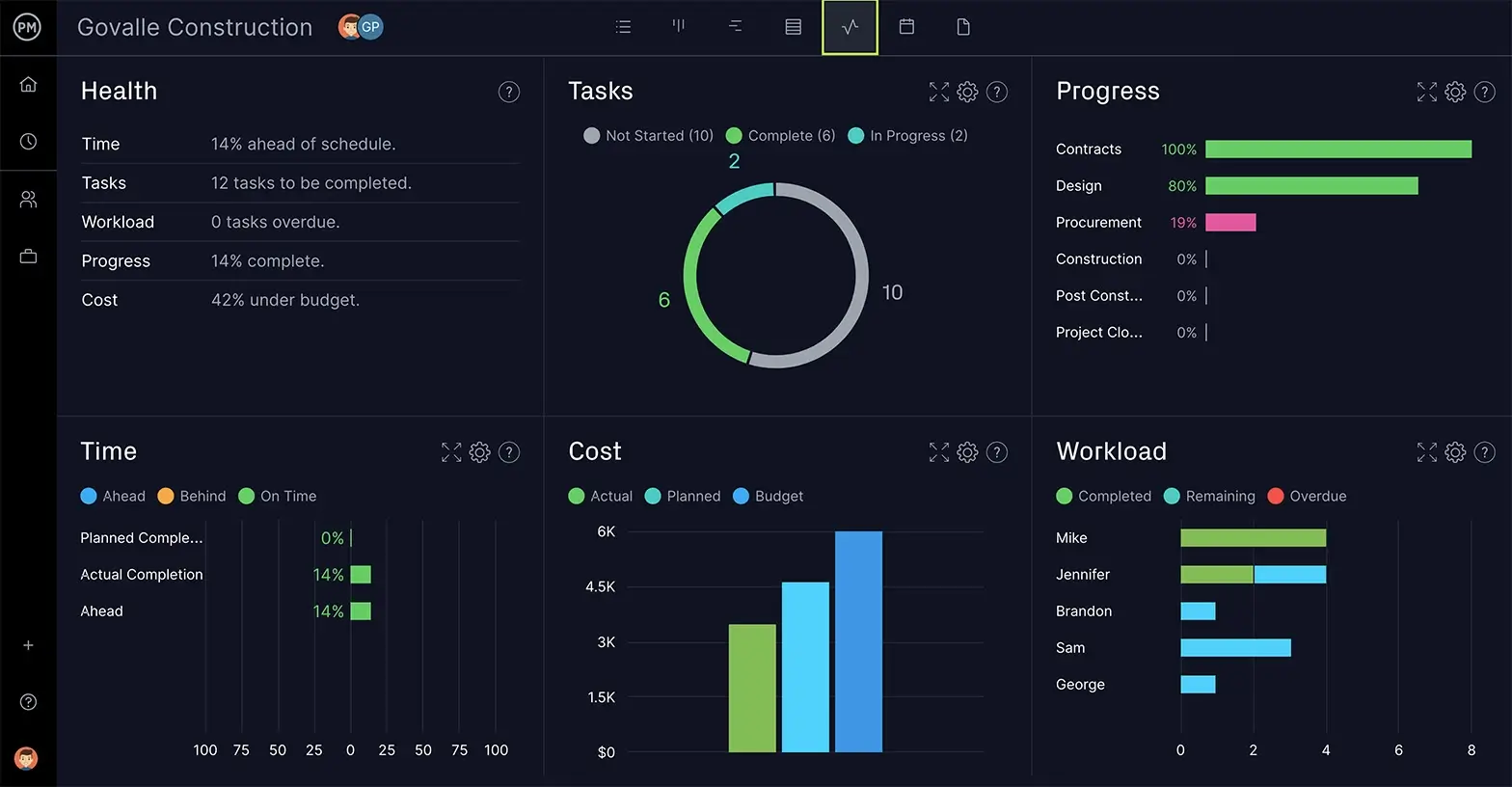
Get a Excessive-Stage View With Actual-Time Dashboards
Our software program helps venture managers and their groups work extra effectively and productively, and that very same expertise might be utilized right here to assist run a RAID log extra effectively. Our software tracks dangers, progress and modifications in your venture with a real-time dashboard. There’s no time-consuming setup obligatory as with light-weight instruments. We’re prepared if you end up with easy-to-read graphs and charts that monitor time, prices and extra in actual time and extra precisely than a RAID log.

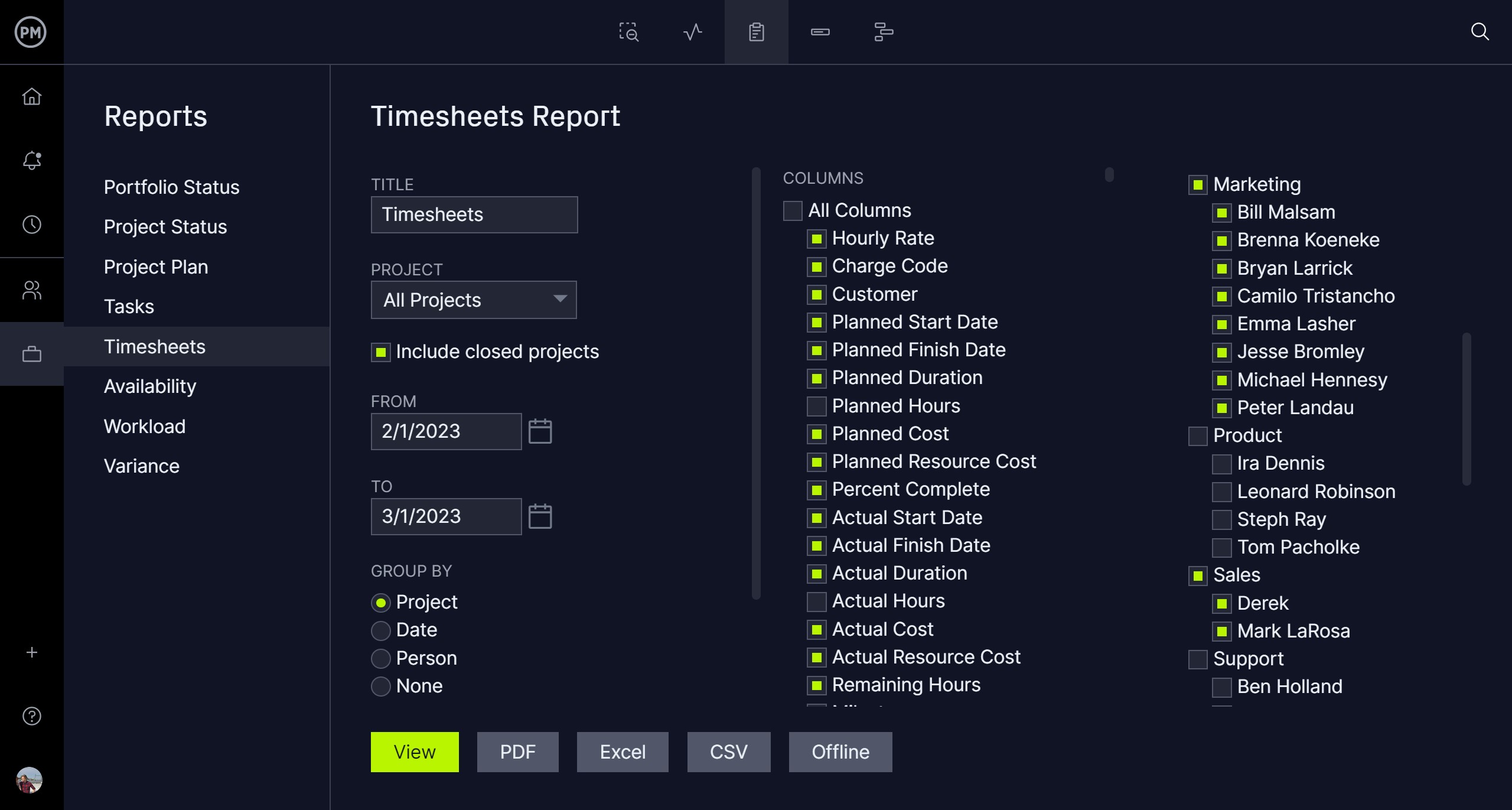
Go Deeper Into the Information With Customizable Reviews
If you wish to get extra particulars than a dashboard can present, we have now many experiences that may be generated with a few keystrokes. Each report, from standing and portfolio experiences to variance, workload, time, price and extra, might be filtered to point out solely the info you need—even filtered by tag so you possibly can monitor dangers, points and modifications to the venture. You may as well simply share the experiences to maintain stakeholders up to date.

That’s solely a few of the options you’ll discover. Managing threat means you want strong useful resource administration instruments. Our software program will help you already know the supply of your staff after which use a color-coded workload chart to stability their allocation and hold groups productive. No different software program offers you this a lot management with such easy-to-use instruments.
ProjectManager could make the helpful RAID log much more helpful by making it easy to trace the problems, dangers and extra in your venture. Its cloud-based software program has instruments comparable to a real-time dashboard and presents a collaborative platform making it straightforward for staff members to replace their standing, so that you’re all the time getting a present view of the venture. Get began with ProjectManager immediately totally free.







